Kimlik Yönetiminde
ideal Çözüm
İnsan Kaynakları biriminizde kullandığınız uygulamadan aldığımız personel bilgileri ile Active Directory üzerindeki tüm kullanıcı ve grup hesaplarınız otomatik tanımlanır.
Active Directory ile entegrasyonu olmayan uygulamalarınızla da senkronizasyon sağlanarak tüm uygulamalara tek kullanıcı kodu ve şifre ile bağlanılması sağlanır.
ideal IDM Nedir?
İnsan Kaynakları uygulamalarında tanımlanan personel bilgilerini, bilgi sistemleri erişim yetkilendirmesini yöneten Active Directory (AD) sistemi ve diğer uygulamalarınız ile entegre eden bir senkronizasyon uygulamasıdır.
Entegre
Yetki Grupları
Senkronize
Otomasyon
idealleri olan bir IT’ci
IT’ciler, IT’cilerimiz. Onlar kim bilir hangi güvenlik açıklarını kapamayı, hangi yazılımları geliştirmeyi hak ediyorlar. Peki biz ne yapıyoruz? Onları okunmayan giriş kartları ile, çalışmayan projeksiyon cihazları ve bazen de yazmayan printerlar ile meşgul ediyoruz.
Etmiyor muyuz?
ideal Nasıl çalışır?
İnsan Kaynakları departmanının ilgili personel uygulamasına çalışan bilgilerini girmesinin ardından ideal IDM bu bilgileri Active Directory ve özel uygulamalarınızla otomatik olarak senkronize eder.
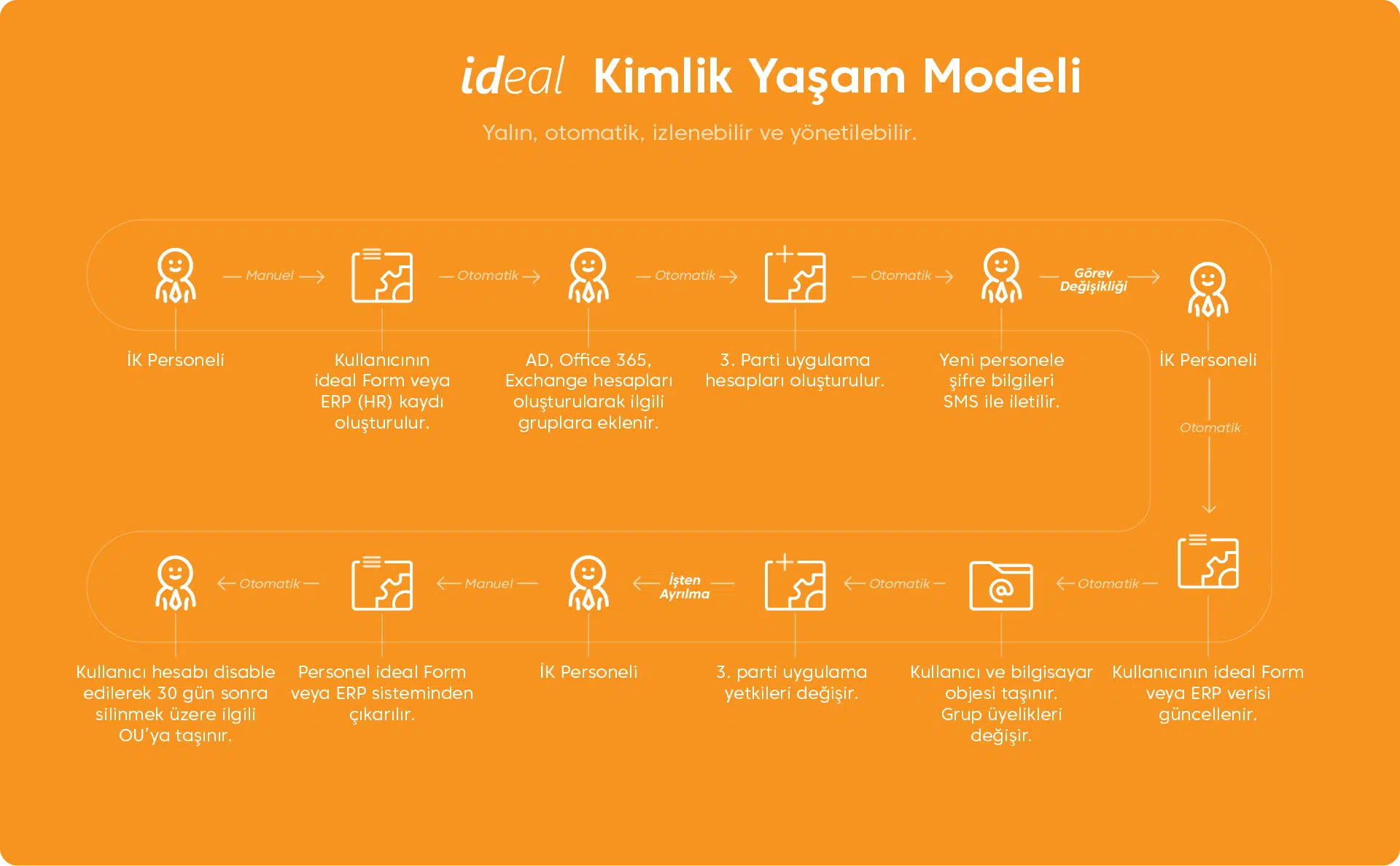
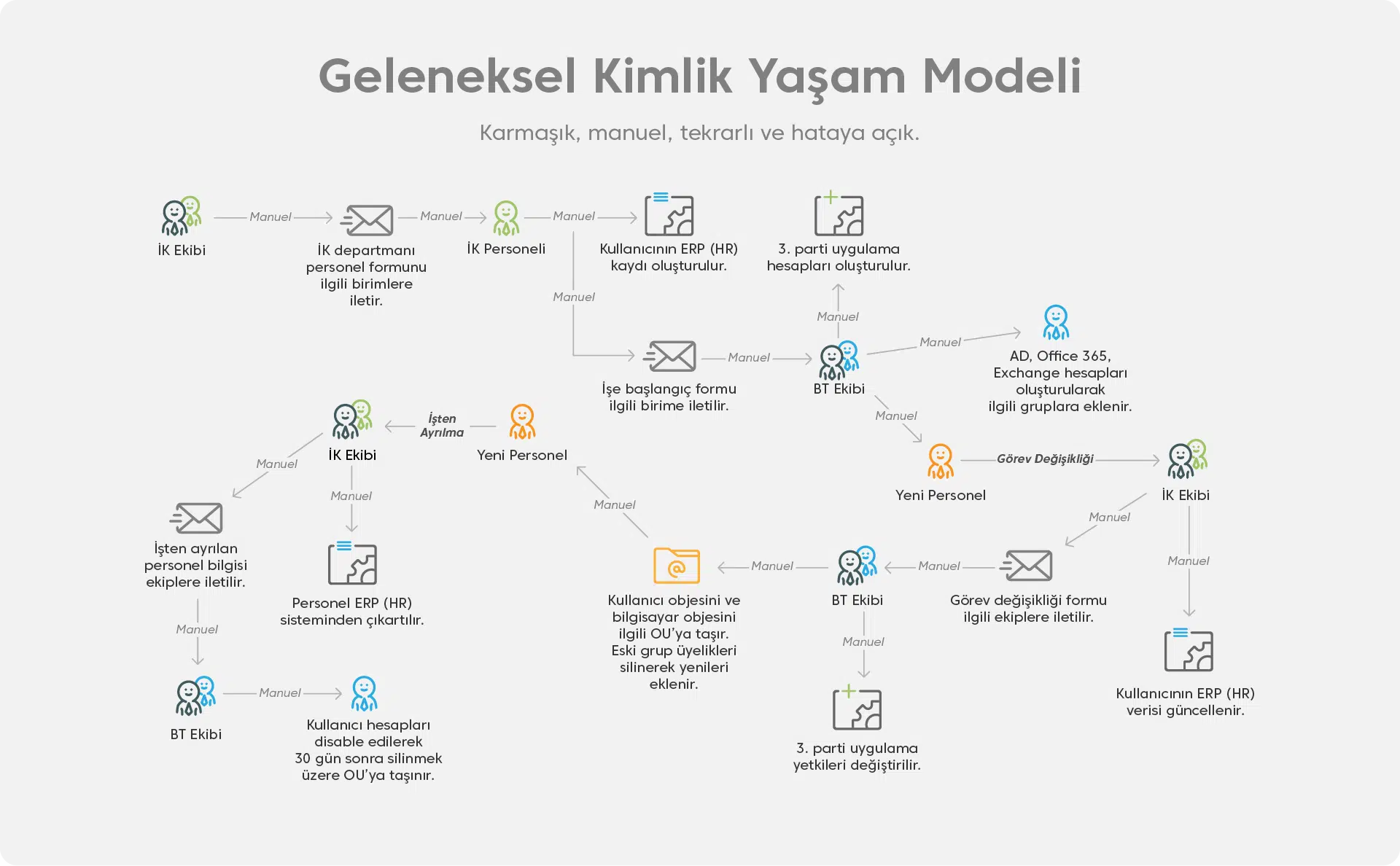
Kimlik Yaşam Modeli Nasıl Olmalı?
Yerli ve ideal Çözüm

Data Market Bilgi Hizmetleri A.Ş.
Halihazırda kullanılan global ürünlerin yerine ideal IDM ile daha iyisini sunabilmek bizim için gurur verici.
10+ Yıl
20+ Yıl
Yazılım ve entegrasyon projelerinde uzmanlık

Neden İhtiyaç Var?
İşe Alım
Pozisyon Değişikliği
Neden İhtiyaç Var?
İşten Ayrılma
Vekaleten Atamalar
- Operasyonel Verimlilik
- Adminler için sistemin tek bir yerden kolay yönetimi
- Detaylı log izleme
- Hazır webformlar
- Hazır raporlar
- Kolay dashboard tasarımı ve webden yayınlama
- Özelleştirme
- Hazır connectorler
- Custom connector yazabilme
- Kod editörü sağlama
- Kolay form tasarımı, script ekleyebilme
- Çoklu dil yeteneği
- Güvenlik & Uyumluluk
- Yetki matrisi
- Onayları izleyebilme
- Exception tanımlayabilme
- Tek şifre senkronizasyonu
- Self servis şifre yönetimi
- Uygun Maliyet
- Yerli kaynak kullanımı
- Paket çözüm, kurulum ve güncelleme kolaylıkları
- Türk Lirası olarak fiyatlandırma
- Kademeli yaygınlaştırma yönetimi
Entegrasyonlar
ideal, güçlü API desteği sayesinde paket uygulamalar ve kurum içi geliştirilen özel uygulamalarla kolay entegrasyon imkanları sunar.
Hazır Connectorleri ile entegrasyon süresini kısaltır. Custom Connector yetenekleri ile özel entegrasyon ihtiyaçlarına cevap verir.









Size özel bir entegrasyon ihtiyacınız mı bulunuyor?
Webinarlar
Neden Dijital bir Kimlik Yönetimi Çözümü Kullanmalısınız?
Dijital Dönüşümde Kimlik Yönetimi Olmazsa Olmaz – Neden / Nasıl?
Referanslar
ideal IDM'i kullanarak verimliliğini arttıran firmalar
Otomotiv yan sanayi metal sektöründe Türkiye’de ulaştığı başarıları Dünya ölçeğine taşıyan Beyçelik Gestamp A.Ş, yenilikçi yüzü ve son teknolojileri barındıran yatırımlarıyla ana sanayilerin tercih ettiği bir kuruluştur. Sektörünün liderleri arasında olan Beyçelik Gestamp A.Ş, kimlik ve yetki yönetimi çözümü için ideal IDM’i tercih etti.
Müşteri hizmetleri alanında lider bir marka haline gelen AssisTT, çağdaş ve yenilikçi yaklaşımlarıyla sektörde fark yaratıyor. Müşteri memnuniyetini ve kaliteli hizmeti odağına alan Assistt, yaklaşık 20.000 çalışanının kimlik yönetimini ideal IDM ile yapıyor.
Türkiye’de doğup, global bir marka olma amacını gerçekleştiren DeFacto, yeniliği ve yenilenmeyi kurum kültürü olarak benimseyen kaliteli ve özgün tasarımlarını dünyanın dört bir yanındaki tüketicilerle buluştururken kimlik yönetimini ideal IDM ile yapıyor.
İçerikler:
Çalışanlarınızın dijital kimliklerinin yönetimini uçtan uca nasıl yapabileceğinizi anlattığımız içeriklerimizi inceleyerek aklınızdaki sorulara cevap bulabilirsiniz.